2022 (Matt Hobbs) Update to this original article by Masanori Nakamura
As per Masa’s original findings, certain things need to be done on a base installation for OpenLDAP to work with PowerFlex, most notably the “memberOf” attribute needs to be set and configured.
In order to test this out myself in a quick(ish) way, I ended up downloading the Turnkey OpenLDAP appliance to spin up a quick VM for this purpose – https://www.turnkeylinux.org/openldap (As of this post I used the current version 16.1)
The deployment of the VM is quite straight forward, but getting the finer touches done is what we will discuss here.
The first thing you will need to do is get memberOf working, and the guidance at this site was spot on for me. This was especially relevant for the Turnkey 16.1 appliance as the backend DB has changed which made the earlier links in Masa’s post no longer work.
The other great thing about Turnkey is that you also get the nice phpLDAPadmin GUI:
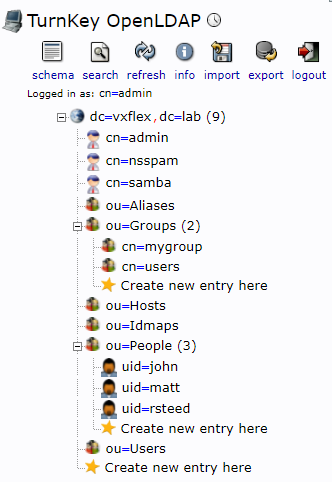
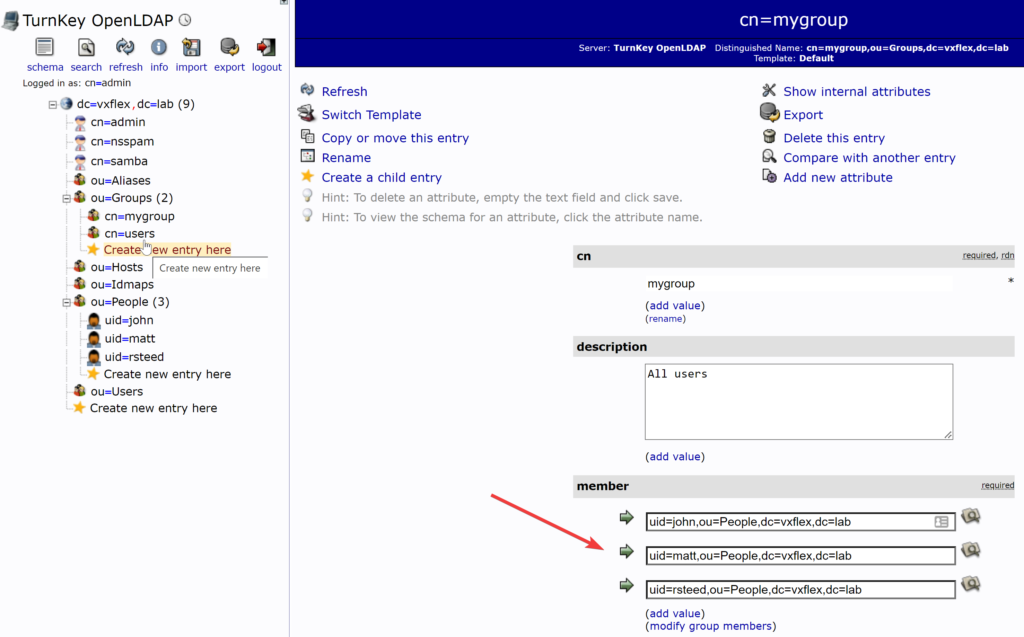
This is where I created my custom group (mygroup), and my custom OU (People), and my users (john, matt, rsteed). When creating these new users, it’s also important if you are going to use a “cn”, or a “uid” for them. I chose to go with the uid.
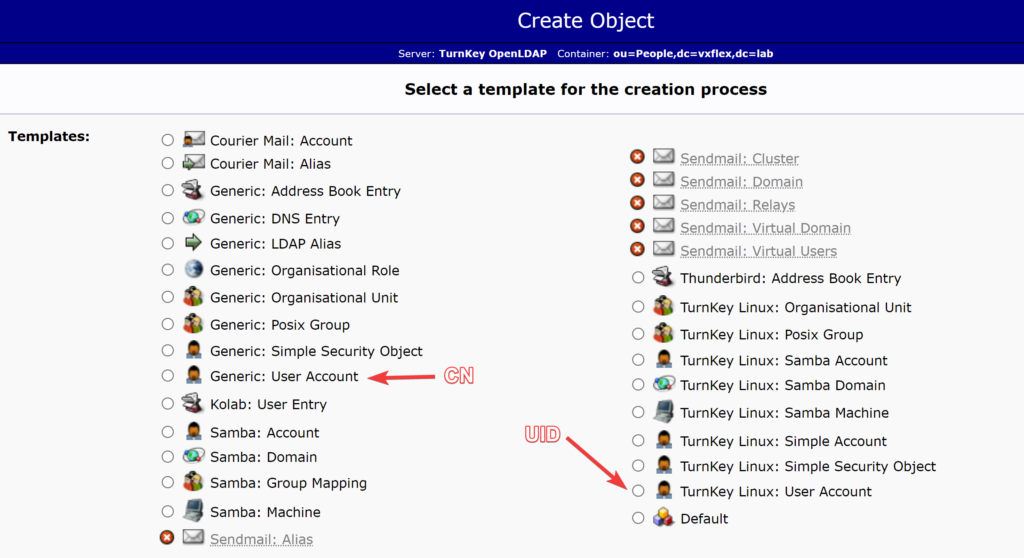
After you have created your users, you will then need to add them to your custom group:
Next is the final trick of getting the working LDAP entry in the PowerFlex MDM configuration. This is what I ended up using:
scli --add_ldap_service --ldap_service_uri LDAP://ldap.vxflex.lab:389 --ldap_base_dn "dc=vxflex,dc=lab" --ldap_service_name "vxflex" --username_dn_format "uid=[USER],OU=People,DC=vxflex,DC=lab" --search_filter_format "(&(objectClass=inetOrgPerson)(uid=[USER])(memberOf=[GROUP]))" LDAP uri defined with unsecured protocol. Press 'y' and then Enter to confirm: y
Successfully added an LDAP service. Object ID 26b3911300000000 with Name: vxflex, URI: LDAP://ldap.vxflex.lab:389 and base DN: dc=vxflex,dc=lab
scli --assign_ldap_groups_to_roles --ldap_service_id 26b3911300000000 --administrator_role_dn "cn=mygroup,ou=Groups,dc=vxflex,dc=lab" --allow_overwrite
Assignment of roles to LDAP groups completed successfully
From there just give it a quick test:
scli --login --username rsteed --ldap_authentication
Enter password:
Logged in. User role is Administrator. System ID is 3fbfb7e1558d5a0f
And we are in business!
If things don’t go so smoothly for you, you may be able to monitor the MDM trace logs to get some ideas, although at this stage I would suggest you log an SR# to get additional support as getting LDAP working in your environment can be complex given that each environment is unique in some shape or form.
tail -F /opt/emc/scaleio/mdm/logs/trc.z.0 -n 0 | /opt/emc/scaleio/mdm/bin/trace_decompress -I --stdout | grep ldap
I will further update this document in the future (time and interest permitting) to include LDAPS instead for additional security. Hopefully this was a useful update for now, but please continue reading the original article for further general guidance on this topic if you need it.
2020 – Original Article
LDAP configuration/schema
VxFlex OS identifies the groups which a user belongs to by search filter like (&(objectClass=inetOrgPerson)(uid=)(memberOf=)).
Therefore we need to enable “groupofNames” objectclass and to include groupofNames objectclass in each groups. This then creates a memberOf attribute to the member, when we add a member to the group.
For more information on this critical pre-requisite, please see:
- How to enable MemberOf using OpenLDAP
- OpenLDAP Software 2.4 Administrator’s Guide
- Man slapo-memberof(5)
The MemberOf attribute is not shown, if we don’t specify the attribute:
[root@ldap ldif]# ldapsearch -LLL -h localhost -x -D cn=config -w admin -b "dc=example,dc=com" "(cn=monitor)"
dn: cn=monitor,ou=Group,dc=example,dc=com
objectClass: groupOfNames
cn: testgroup
cn: monitor
member: uid=test0,ou=People,dc=example,dc=com
member: uid=test1,ou=People,dc=example,dc=com
member: uid=test2,ou=People,dc=example,dc=com
member: uid=test3,ou=People,dc=example,dc=com
[root@ldap ldif]# ldapsearch -LLL -h localhost -x -D cn=config -w admin -b "dc=example,dc=com" "(uid=test1)"
dn: uid=test1,ou=People,dc=example,dc=com
objectClass: inetOrgPerson
sn: nakamura
cn: masanori
uid: test1
mail: test1@example.com
[root@ldap ldif]# ldapsearch -LLL -h localhost -x -D cn=config -w admin -b "dc=example,dc=com" "(uid=test1)" uid memberOf
dn: uid=test1,ou=People,dc=example,dc=com
uid: test1
memberOf: cn=monitor,ou=Group,dc=example,dc=com
[root@ldap ldif]#VxFlex OS settings
There are 3 things to do:
- CLI, REST API
- Installation Manager / Gateway
- LIA
CLI, REST API
(REST API gets token from MDM through Gateway)
[root@vxflexos-1 ~]# scli --add_ldap_service --ldap_service_uri "ldap://ldap.example.com" --ldap_base_dn "dc=example,dc=com" --username_dn_format "uid=*,ou=People,dc=example,dc=com" --object_class_attribute inetOrgPerson --user_attribute_name uid --member_of_attribute_name memberOf --ldap_service_name myldap --disable_recursive_search
LDAP uri defined with unsecured protocol. Press 'y' and then Enter to confirm: y
Successfully added an LDAP service. Object ID 8ddd51eb00000000 with Name: myldap, URI: ldap://ldap.example.com and base DN: dc=example,dc=com
[root@vxflexos-1 ~]# scli --assign_ldap_groups_to_roles --ldap_service_name myldap --backend_config_role_dn cn=backend,ou=Group,dc=example,dc=com --frontend_config_role_dn cn=frontend,ou=Group,dc=example,dc=com --monitor_role_dn cn=monitor,ou=Group,dc=example,dc=com --administrator_role_dn cn=administrator,ou=Group,dc=example,dc=com
Assignment of roles to LDAP groups completed successfully
[root@vxflexos-1 ~]# scli --set_user_authentication_method --native_and_ldap_authentication
Authentication method changed successfully
[root@vxflexos-1 ~]# scli --query_user_authentication_properties
------------------------------------------------------------
User authentication method: Native and LDAP
System has 1 configured LDAP services
------------------------------------------------------------
LDAP service ID: 8ddd51eb00000000
LDAP service name: myldap
LDAP service URI: ldaps://ldap.example.com
Users base DN: dc=example,dc=com
User search filter: (&(objectClass=inetOrgPerson)(uid=<USER>)(memberOf=<GROUP>))
Username DN format: uid=*,ou=People,dc=example,dc=com
LDAP service has 4 configured groups.
Role: Administrator
Group DN: cn=administrator,ou=Group,dc=example,dc=com
Role: BackEndConfigure
Group DN: cn=backend,ou=Group,dc=example,dc=com
Role: Monitor
Group DN: cn=monitor,ou=Group,dc=example,dc=com
Role: FrontEndConfigure
Group DN: cn=frontend,ou=Group,dc=example,dc=com
------------------------------------------------------------
[root@vxflexos-1 ~]# scli --login --username test1 --ldap_authentication --password P@ssw0rd
Logged in. User role is Monitor. System ID is 7356df847ec9ac0f
[root@vxflexos-1 ~]#Notes:
1. –disable_recursive_search is needed to set “User search filter” to make the format understandable by OpenLDAP.
Installation Manager / Gateway
[root@gateway ~]# /opt/emc/scaleio/gateway/bin/FOSGWTool.sh --reset_ldap_properties --server_url_list "ldap://ldap.example.com" --base_dn_list "dc=example,dc=com" --group_name_list "cn=administrator,ou=Group,dc=example,dc=com" --dn_format_list "uid=<USER>,ou=People,dc=example,dc=com" --filter_list "(&(objectClass=inetOrgPerson)(uid=<USER>)(memberOf=<GROUP>))" --create_default_lockbox
[root@gateway ~]# systemctl restart scaleio-gateway.service
[root@gateway ~]#Notes:
1. Use <USER> to associate with the user name of input at Gateway.
2. login to Gateway by user like: test0@<base_dn>.
LIA
1. Edit /opt/emc/scaleio/gateway/webapps/ROOT/WEB-INF/classes/gatewayUser.properties.
INF/classes/gatewayUser.properties and restart Gateway
# properties for add lia ldap server
lia.ldap.objectClassAttr=inetOrgPerson
lia.ldap.userIdAttrName=uid
lia.ldap.memberOfAttrName=memberOf
lia.ldap.replicationExisting=
lia.ldap.disableRecursiveSearch=true
lia.ldap.usernameDnFormat=uid=*,ou=People,dc=example,dc=com
lia.ldap.authorizerDn=2. Restart Gateway.
[root@gateway ~]# systemctl restart scaleio-gateway.service
[root@gateway ~]#3. Setting at Maintain tab of Gateway.
- Execute “Retrieve system topology”
- At Security Setting , execute “Add LDAP Server”


- At Security Setting, execute “Change LIA authentication method to LDAP”
- Once Cancel the job. Then execute “Retrieve system topology” again
- Check LIA authentication set LDAP

SSL/TSL setting
By default, OpenLDAP server uses self-signed certificate. We need to set LDAP client to accept untrusted certificates or resister LDAP server’s certificate.
There two thins to do:
- CLI, REST API, LIA
- Gateway
CLI, REST API, LIA
CLI, REST API and LIA use openldap client config is from /etc/openldap/ldap.conf.
Option 1. To accept untrusted certificates, check /etc/openldap/ldap.conf
TLS_REQCERT allowOption 2. To register the LDAP server’s certificate, copy the LDAP server’s certificate to /etc/openldap/certs.
We need to configure on all nodes on which MDM and LIA run. And after we change the settings we need to restart MDM and/ or LIA.
Restart MDM
[root@vxflexos-1 ~]# /opt/emc/scaleio/mdm/bin/delete_service.sh
Removed symlink /etc/systemd/system/multi-user.target.wants/mdm.service.
[root@vxflexos-1 ~]# /opt/emc/scaleio/mdm/bin/create_service.sh
Created symlink from /etc/systemd/system/multi-user.target.wants/mdm.service to /usr/lib/systemd/system/mdm.service.
[root@vxflexos-1 ~]#Restart LIA
[root@vxflexos-1 ~]# /opt/emc/scaleio/lia/bin/delete_service.sh
Removed symlink /etc/systemd/system/multi-user.target.wants/lia.service.
[root@vxflexos-1 ~]# /opt/emc/scaleio/lia/bin/create_service.sh
Created symlink from /etc/systemd/system/multi-user.target.wants/lia.service to /usr/lib/systemd/system/lia.service.
[root@vxflexos-1 ~]#Gateway
Gateway uses ldap client in Java. So we need to store the LDAP server’s certificate in lockbox for Gateway.
Copy LDAP server’s certificate to Gateway node, then import it to the lockbox and restart Gateway.
[root@gateway ~]# keytool -import -alias ldapserver -file "path_to_ldap_server.crt" --keystore "/opt/emc/scaleio/gateway/webapps/ROOT/WEB-INF/classes/certificates/truststore.jks" --storepass changeit
所有者: CN=ldap.example.com, OU=Example, O=Example Ltd, L=Shibuya-ku, ST=Tokyo, C=JP
発行者: CN=ldap.example.com, OU=Example, O=Example Ltd, L=Shibuya-ku, ST=Tokyo, C=JP
シリアル番号: fe602af83ef96ae3
有効期間の開始日: Sat Oct 26 10:54:45 JST 2019 終了日: Tue Oct 23 10:54:45 JST 2029
証明書のフィンガプリント:
MD5: 35:94:C1:CC:C8:FE:DE:1D:D7:F4:54:56:F9:CC:5E:0A
SHA1: E4:24:CA:B1:E6:22:00:BA:65:BD:A4:92:56:4D:B0:F5:9A:99:7C:6B
SHA256: 66:E2:F1:70:86:96:7D:7E:5A:04:F5:CB:12:46:77:44:97:04:C9:BE:40:D0:70:BE:30:86:79:3B:E7:E1:E9:BE
署名アルゴリズム名: SHA256withRSA
サブジェクト公開鍵アルゴリズム: 2048ビットRSA鍵
バージョン: 1
この証明書を信頼しますか。 [いいえ]: Y
証明書がキーストアに追加されました
[root@gateway ~]# keytool -list -v -keystore "/opt/emc/scaleio/gateway/webapps/ROOT/WEB-INF/classes/certificates/truststore.jks" -alias ldapserver -storepass changeit
別名: ldapserver
作成日: 2020/03/30
エントリ・タイプ: trustedCertEntry
所有者: CN=ldap.example.com, OU=Example, O=Example Ltd, L=Shibuya-ku, ST=Tokyo, C=JP
発行者: CN=ldap.example.com, OU=Example, O=Example Ltd, L=Shibuya-ku, ST=Tokyo, C=JP
シリアル番号: fe602af83ef96ae3
有効期間の開始日: Sat Oct 26 10:54:45 JST 2019 終了日: Tue Oct 23 10:54:45 JST 2029
証明書のフィンガプリント:
MD5: 35:94:C1:CC:C8:FE:DE:1D:D7:F4:54:56:F9:CC:5E:0A
SHA1: E4:24:CA:B1:E6:22:00:BA:65:BD:A4:92:56:4D:B0:F5:9A:99:7C:6B
SHA256: 66:E2:F1:70:86:96:7D:7E:5A:04:F5:CB:12:46:77:44:97:04:C9:BE:40:D0:70:BE:30:86:79:3B:E7:E1:E9:BE
署名アルゴリズム名: SHA256withRSA
サブジェクト公開鍵アルゴリズム: 2048ビットRSA鍵
バージョン: 1
[root@gateway ~]# systemctl restart scaleio-gateway.service
[root@gateway ~]#